What is an advanced persistent threat (APT)?
- Attack library
- Advanced persistent attack
- What is an advanced persistent threat (APT)?
- Stages of an APT attack
- Well-known APT attacks examples
- Indicators for detecting an APT
- How can you prevent an APT attack?
- How to protect against APTs
- How Log360 can help detect and mitigate an APT
What is an advanced persistent threat (APT)?
An APT is a sophisticated cyberattack where threat actors enter the network by exploiting a system's vulnerabilities, and remain undetected for a significant time. This cyber espionage attack is designed to extricate valuable data, and avoid detection for as long as possible.
In accordance with the attackers' objective, the outcome of an APT varies. These are some common results of an APT:
- Data theft
- Persistent access
- Significant damage to the system
Stages of an APT attack
An APT is a meticulously designed cyberattack to infiltrate a network and enable the attacker to remain undetected for an extended duration.
- Infiltration: This occurs when adversaries gain entry into the victim’s network using social engineering techniques, or by exploiting vulnerabilities and injecting malware. During this stage, a blend of clever tactics (such as spear phishing privilege escalation, and malware attacks), and a comprehensive grasp of the target's vulnerabilities are combined to create an initial entry point that ensures an enduring and discreet presence.
- Lateral movement: After attaining an initial foothold in the network, adversaries move through it laterally to identify other vulnerabilities and establish additional points of compromise. This ensures that the attack can continue even if some of the points are detected.
- Exfiltration: Adversaries commonly secure stolen data within a protected network location by accumulating a sufficient amount before initiating extraction, known as "exfiltration". Employing tactics such as a denial-of-service attack, cybercriminals divert the attention of the security team, ensuring a seamless exfiltration process.The compromised network remains vulnerable, meaning that the hackers could potentially return at any time.
Well-known APT attacks examples
- 2003
Titan Rain
In 2003, APT attacks originated in China against the United States government with the aim of stealing state secrets and sensitive military data. The US Department of Defense, the United Kingdom Ministry of Defense, NASA, and FBI systems were targets.
- 2009
Ghostnet
Detected in 2009, GhostNet was an espionage operation carried out in China to infiltrate sensitive information by activating the microphones and cameras of network computers. This APT attack compromised the computers of the embassies and government bodies of over 100 countries.
- 2010
Stuxnet
In 2010, the Stuxnet worm was planted into the network of Natanz nuclear laboratory in Iran. The virus controlled the working of the centrifuges and damaged them beyond repair. The plant had to decommission around 20% of its centrifuges after the APT attack.
Indicators for detecting an APT
Identifying APTs can be challenging due to their intricate nature. Determining if your organization has fallen victim to APTs is difficult given the meticulous measures cybercriminals take to evade detection. However, there are indicators that can serve as an early alert mechanism for APT occurrences.
- MITRE ATT&CK is a crucial framework for fortifying an organization's defenses against APTs. By leveraging real-world APT instances, this framework not only aids organizations in recognizing the intricate tactics, techniques, and procedures (TTPs) used by APT actors, but also ensures that they identify vulnerabilities specific to such threats. By integrating security solutions based on the MITRE ATT&CK framework, organizations can develop a more robust and resilient cybersecurity strategy tailored to counteract APTs effectively.
- One common indicator is suspicious logon activity from privileged users during non-business hours, which might indicate an APT attack attempting to infiltrate and persist within a system undetected over an extended period. Hence, it's always advisable to keep an eye on the login activity across your network to prevent APTs.
- The widespread presence of backdoor Trojans serves as a clear indicator that an APT situation might be unfolding. When the Trojans are discovered extensively within a network or system, it strongly suggests a highly sophisticated and focused cyberattack. Backdoor Trojans function as hidden entryways, granting unauthorized entry and remote manipulation capabilities. This allows the adversaries to continuously maintain their control over compromised systems in a discreet manner.
How can you prevent an APT attack?
APTs pose a significant obstacle in cybersecurity. As technological progress marches forward and attacks grow increasingly refined, it is imperative for both entities and individuals to embrace a preemptive and multifaceted strategy to protect against APTs. By comprehending the traits of APTs and establishing resilient security protocols, we can effectively traverse the obscurities of the digital realm and shield our digital valuables from determined foes. Here are some ways to prevent APTs threats:
- Analyze and revoke users' excess privileges to sensitive resources within the network.
- Employ user and entity behavior analytics (UEBA), which creates a baseline of normal activities specific to each user and notifies IT teams instantly when there's a deviation from this norm.
- Update antivirus and firewall programs so they can detect and prevent malware and other harmful programs.
- Patch software vulnerabilities regularly.
- Educate employees about phishing emails so they don't click on any suspicious links or attachments.
How to protect against APTs
Deploying a web application firewall (WAF)
- A WAF plays a vital role in safeguarding your organization from APTs. It serves as a protective shield that stands between your web applications and the internet, primarily to scrutinize and sift through incoming traffic to detect malicious actions and recognizable attack methods.
- To keep up with emerging threats, update and fine-tune your WAF rules on a regular basis.
Utilizing threat intelligence
- To stay up to date on APT groups, their TTPs, as well as emerging threats, refer to threat intelligence feeds from credible sources.
- Organizations can use threat alerts to restrict communications from harmful sources as well as automatically trigger a workflow to add blacklisted IPs to the firewall and permanently block them.
Conduct threat hunting
- Identify and segregate potential threats that might evade your initial network security measures to allow for a swift response and reduce the potential harm they could cause.
- Configure real-time alerts to make sure that you get notified when threat patterns recur in your network.
How Log360 can help detect and mitigate an APT
ManageEngine Log360 is a unified SIEM solution that provides continuous monitoring, rapid detection, and effective response capabilities to counter APTs. Its multi-layered approach and advanced analytics contribute to a proactive cybersecurity posture, helping organizations defend against persistent adversaries in the evolving threat landscape.
- Real-time monitoring and detection
- MITRE ATT&CK
- Event correlation
- User and Entity Behavior Analytics (UEBA)
- Automated Alerts and Responses
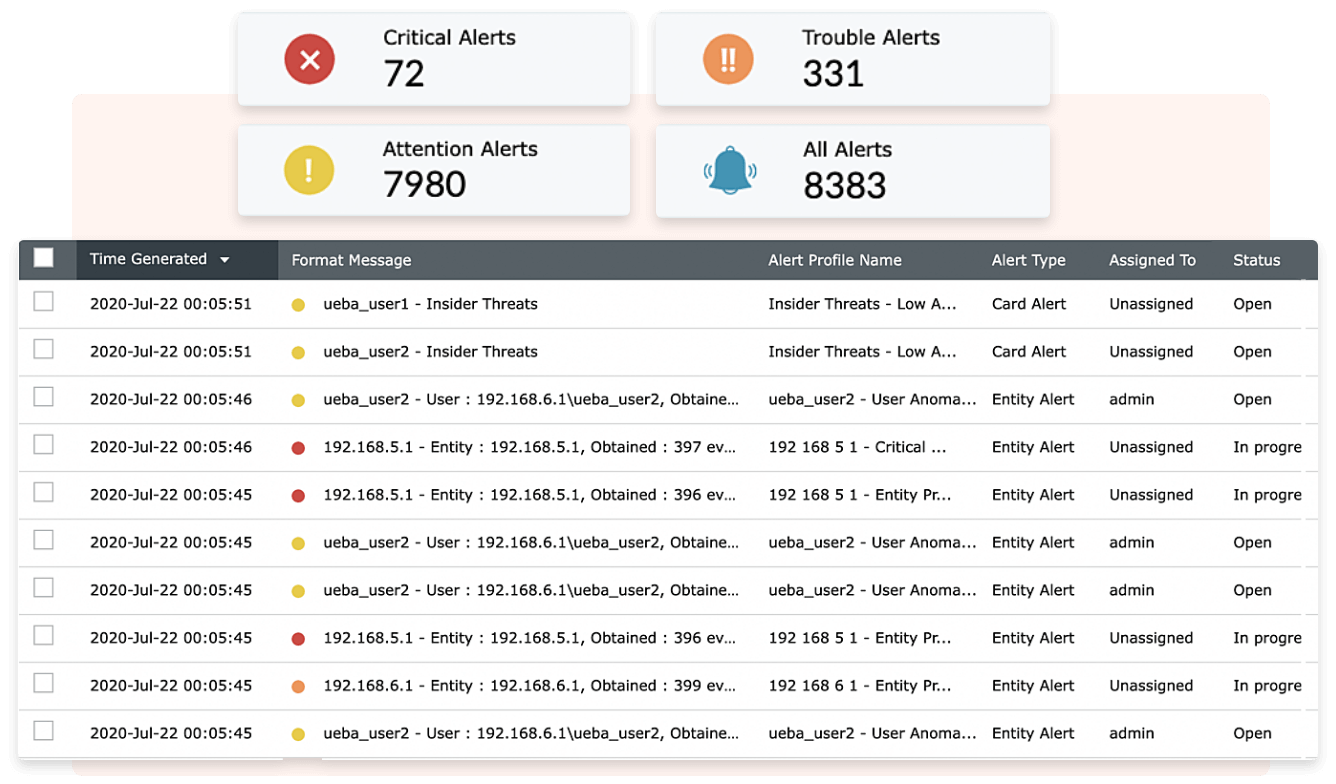
Log360 continuously monitors network activities in real time. This enables early detection of unusual or suspicious activities that could indicate an APT in progress.
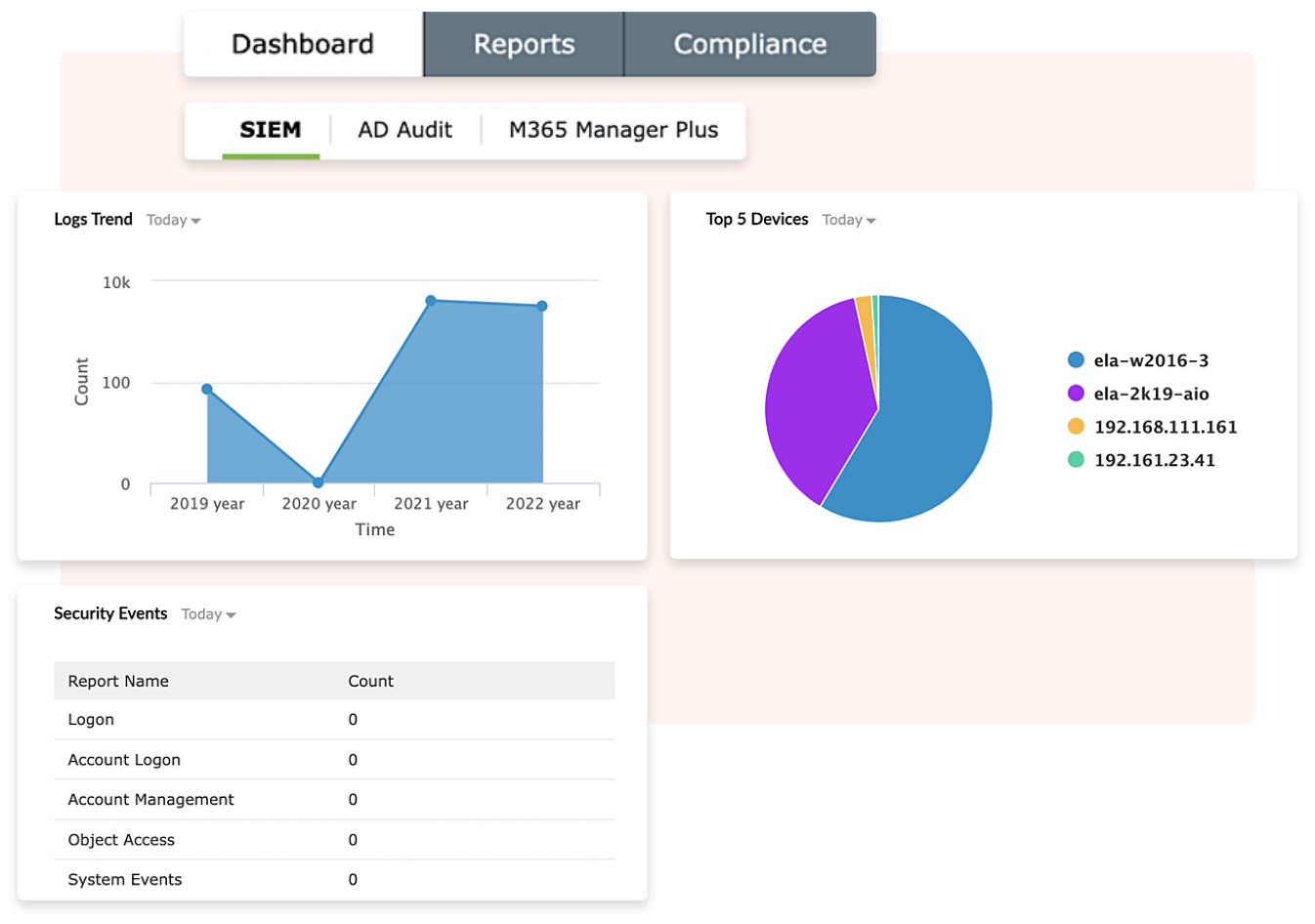
Log360, when implemented with MITRE ATT&CK, provides mitigation steps to stop ATT&CK techniques at every stage and ensure accountability in threat resolution.
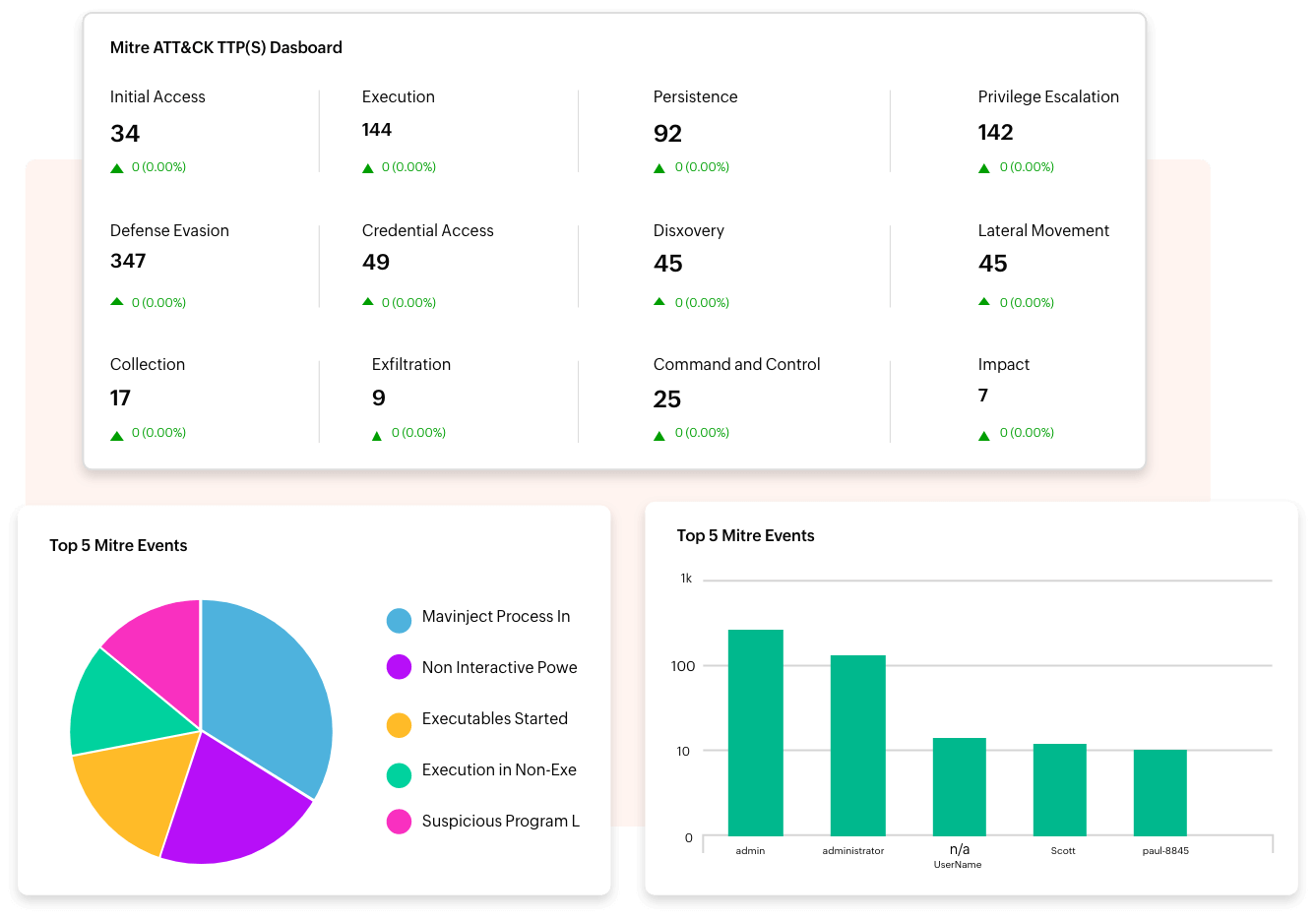
Log360 analyzes and correlates log data from various sources to identify complex attack patterns that may be indicative of an APT attack. This can help security teams detect attacks that might otherwise go unnoticed.
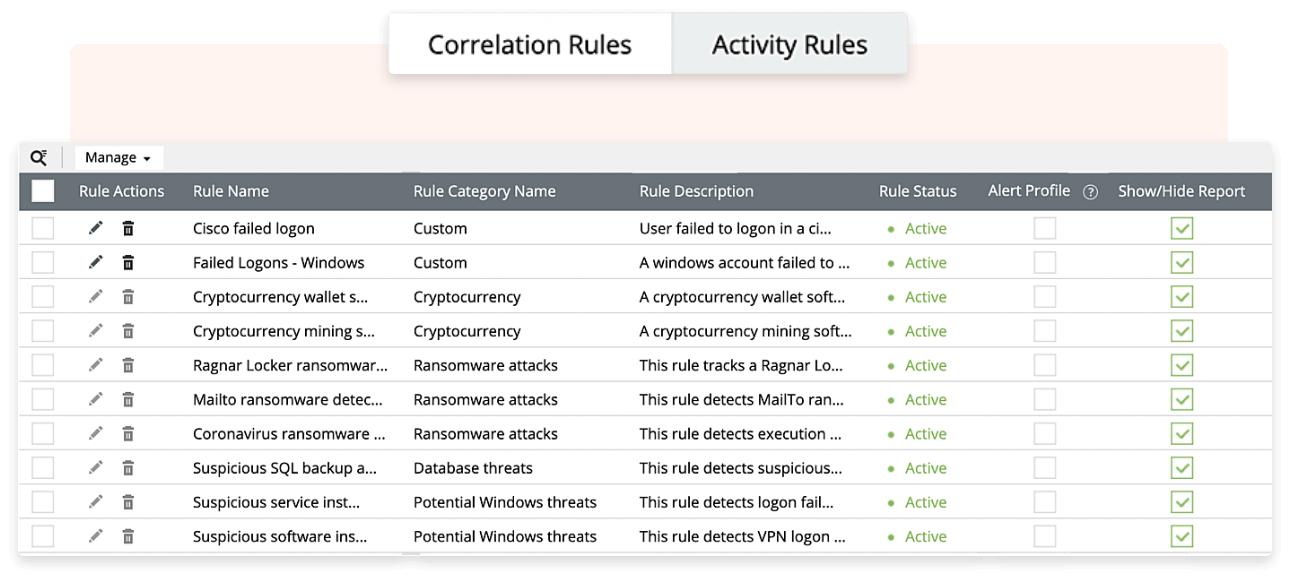
Log360 can analyze user behavior to identify compromised accounts, insider threats, and other malicious activities associated with APTs. This proactive approach enhances the organization's ability to detect and prevent APTs.
Log360 can be configured to send real-time alerts when suspicious activities are detected. Automated responses can also be set up to contain and mitigate APTs before they escalate.