Importing Users from Active Directory
PAM360 integrates with Active Directory in your environment and allows import of users from there. Users logged into the Windows system using their domain account can log into PAM360 directly.
Steps Required
There are three steps involved in importing users from Active Directory:
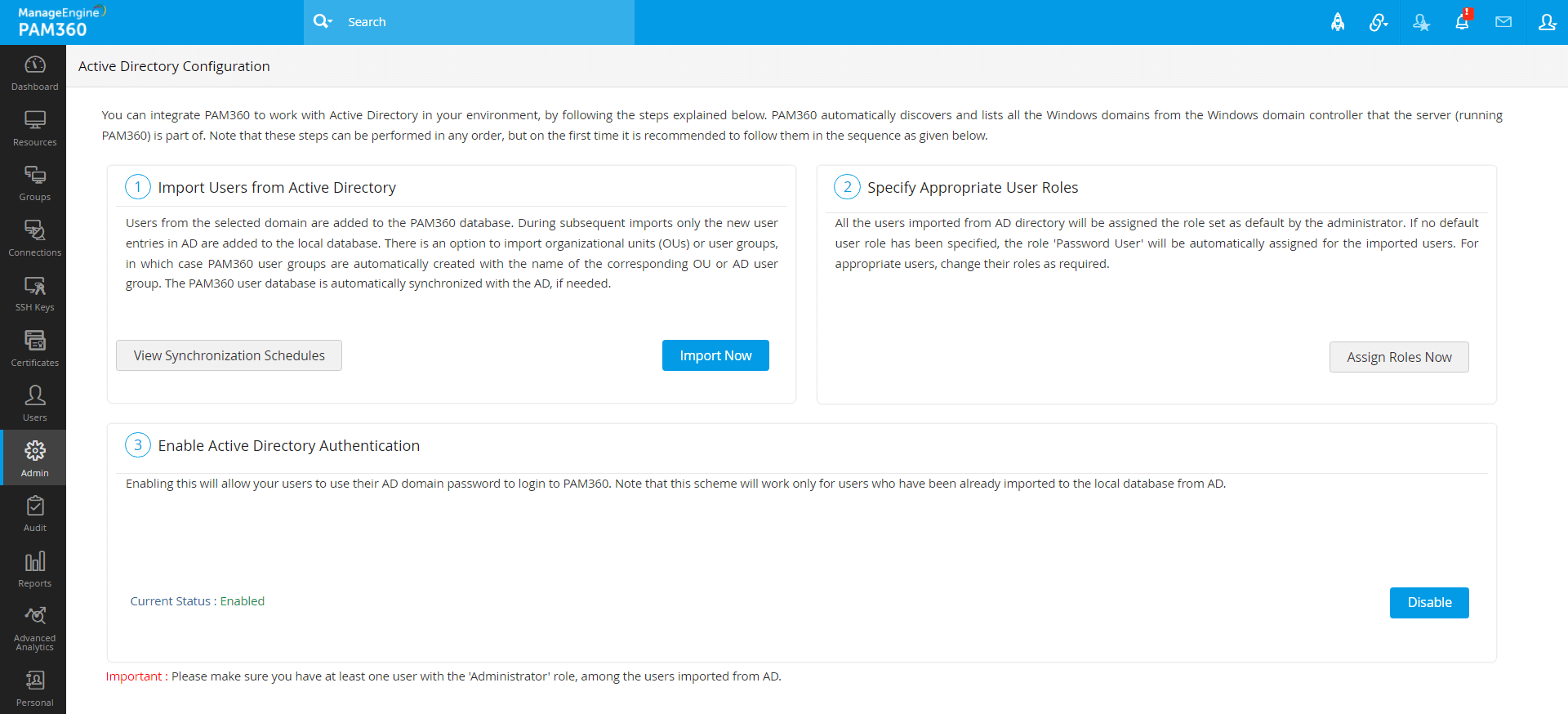
To begin, navigate to Admin >> Authentication >> Active Directory. The Active Directory Configuration page is displayed.
1. Importing Users
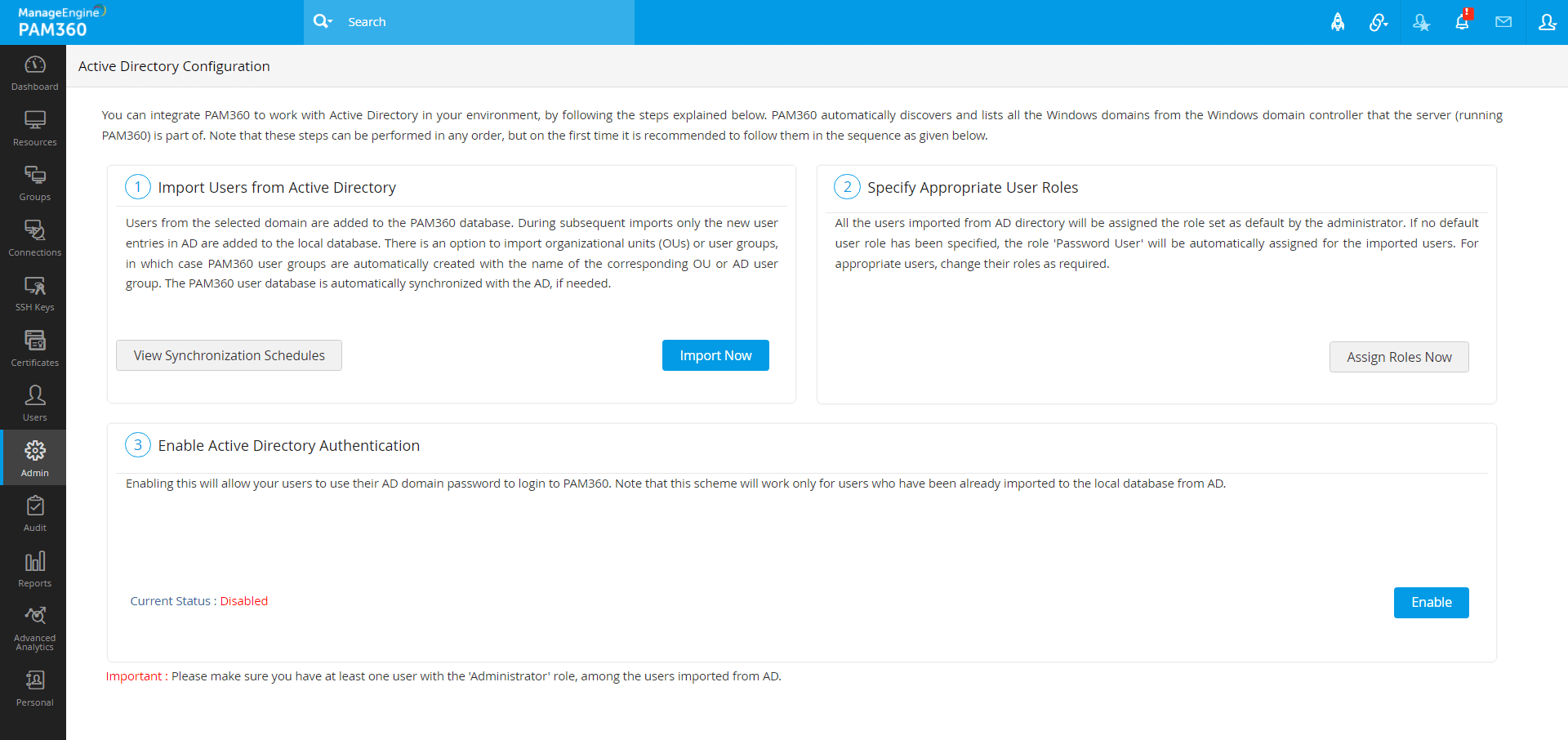
The first step is to provide credential details and import users from Active Directory. PAM360 automatically gets the list of the domains present under the "Microsoft Windows Network" folder of the server of which the running PAM360 is part of. You need to select the required domain from the list and provide necessary domain controller credentials.
To do this:
- Click the Import Now button. Alternatively, you can also access this from Users >> Add user >> Import from Active Directory.
- In the pop-up form that appears, select the required Domain Name, which forms part of the AD from the dropdown.
- Specify the DNS name of the domain controller. This domain controller will be the primary domain controller.
- In case, the Primary Domain Controller is down, Secondary Domain Controllers can be used. If you have secondary domain controllers, specify their DNS names in comma-separated form. One of the available secondary domain controllers will be used. When you use SSL mode, make sure the DNS name specified here matches the CN (common name) specified in the SSL certificate for the domain controller.
- Supply Credentials: Enter a valid user credential (user name and password) having read permission in the domain controller. (If you want to import users from multiple domains, you may enter the username as <DomainName>\<username>. For example, if you want to import DOMAIN A users by giving DOMAIN B username/password, you need to enter the username as <DOMAIN B>\username)).
- Connection Mode: For each domain, you can configure if the connection should be over an encrypted channel for all communication. To enable the SSL mode, the domain controller should be serving over SSL in port 636 and you will have to import the domain controller's root certificate into the PAM360 server machine's certificate store.
- Role: By default, the Password User role is assigned to the users imported from Active Directory. Select the desired role from the drop-down menu to change the user roles. The selected role will be applied to all the users imported from the specified Group(s) or Organizational Unit(s) of the Active Directory.
- Language: You can also change the language for the users you intend to import by utilizing the Language field.
- Two-Factor Authentication: By default, Two-factor authentication is enabled for the users imported from the Active Directory. Disable the toggle button beside the Two-factor authentication field to disable 2FA for the users to be imported.
- Users to Import: By default, PAM360 will populate all the organizational units (OUs) and groups from Active Directory. If you want to import only a particular user, enter the required user name(s) in comma separated form.
- User Groups to Import / OU(s) to Import: Similarly, you can choose to import only specific user groups or organizational units (OUs) from the domain. You can specify the names in the respective text fields in comma-separated form.
- Synchronization Interval: Whenever new users get added to the Active Directory, there is provision to automatically add them to PAM360 and keep the user database in sync. Enter the time interval at which PAM360 has to query the Active Directory to keep the user database in sync. Please ensure you set the sync interval at 3 hours or more based on the number of Groups and OU's imported.
- Click Save. Soon after hitting this "Save" button, PAM360 will save the domain details. During subsequent imports, only the new users entries in AD are added to the local database.
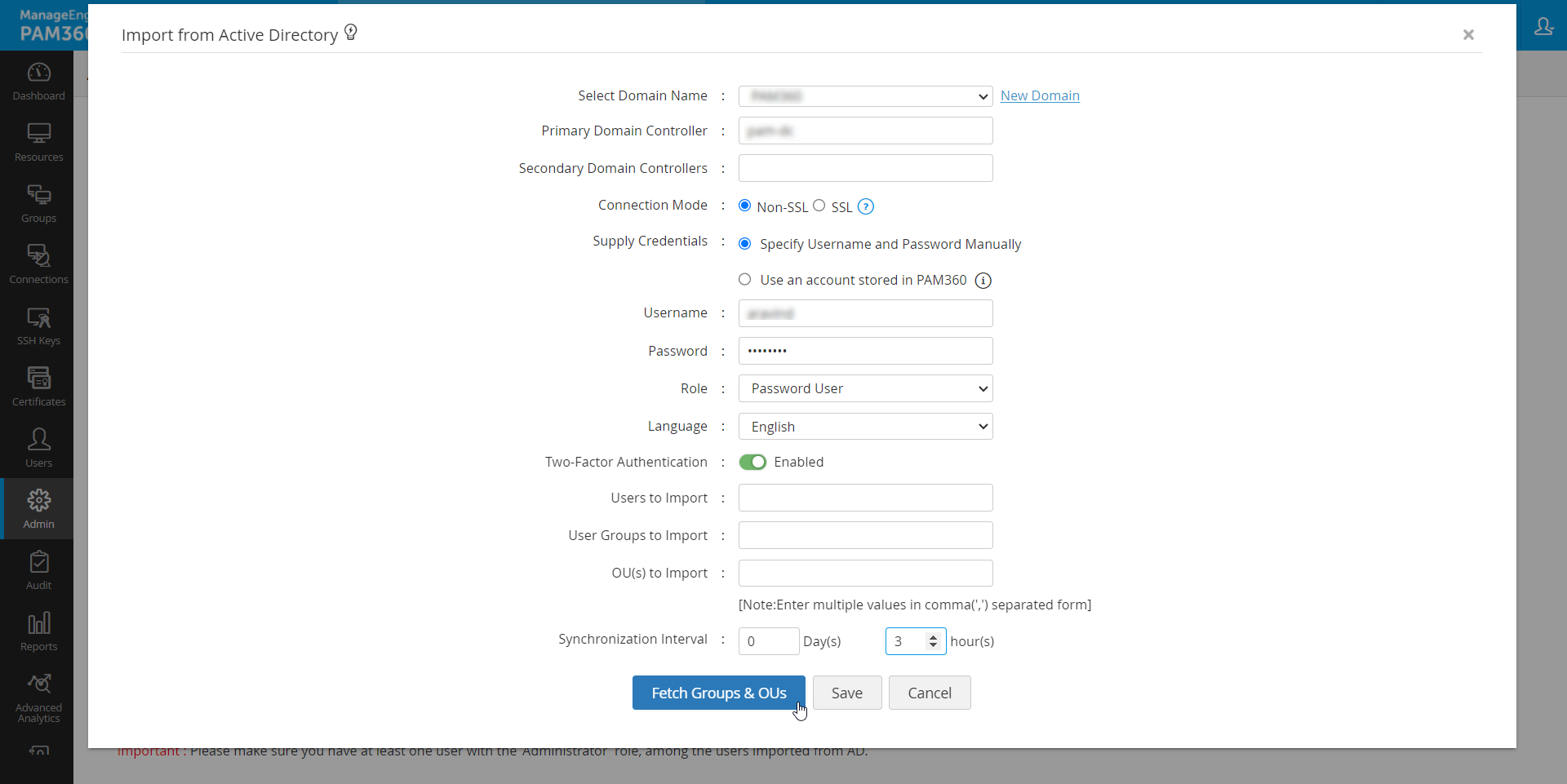
- To look out for specific users, user groups, or organizational units, click the Fetch Groups & OUs button and execute the following actions:
- Select either Groups or Organizational Units and choose the required groups/OUs you want to import from Active Directory. You can also specify roles and languages for each group or organizational unit.
- To view the selected groups, click the View Selected Groups link at the top-right corner.
- After selecting the required groups or organizational units, click Import.
- In case of importing organizational units (OUs) and Active Directory groups, user groups are automatically created with the name of the corresponding OU / AD group.
Note: Initial settings applied during import remain consistent in subsequent schedules unless altered.
Note: If Two-Factor Authentication is disabled globally in the Admin tab, users imported from Active Directory during this period will have the Two-Factor Authentication disabled automatically.
Note: As mentioned above, to enable SSL mode, the domain controller should be serving over SSL in port 636. If the certificate of the domain controller is not signed by a certified CA, you will have to manually import the certificate into the PAM360 server machine's certificate store. You need to import all the certificates that are present in the respective root certificate chain - that is the certificate of the PAM360 server machine and intermediate certificates, if any.
To import domain controller's certificate into PAM360 machine's certificate store: (you can use any procedure that you normally use to import the SSL certificates to the machine's certificate store. One example is given below)
- In the machine where PAM360 is installed, launch Internet Explorer and navigate to Tools >> Internet Options >> Content >> Certificates.
- Click Import.
- Browse and locate the root certificate issue by your CA.
- Click Next and choose the option Automatically select the certificate store based on the type of certificate and install.
- Click Import again.
- Browse and locate the domain controller certificate.
- Click Next and choose the option Automatically select the certificate store based on the type of certificate and install.
- Apply the changes and close the wizard.
- Repeat the procedure to install other certificates in the root chain.
2. Specifying Appropriate User Roles
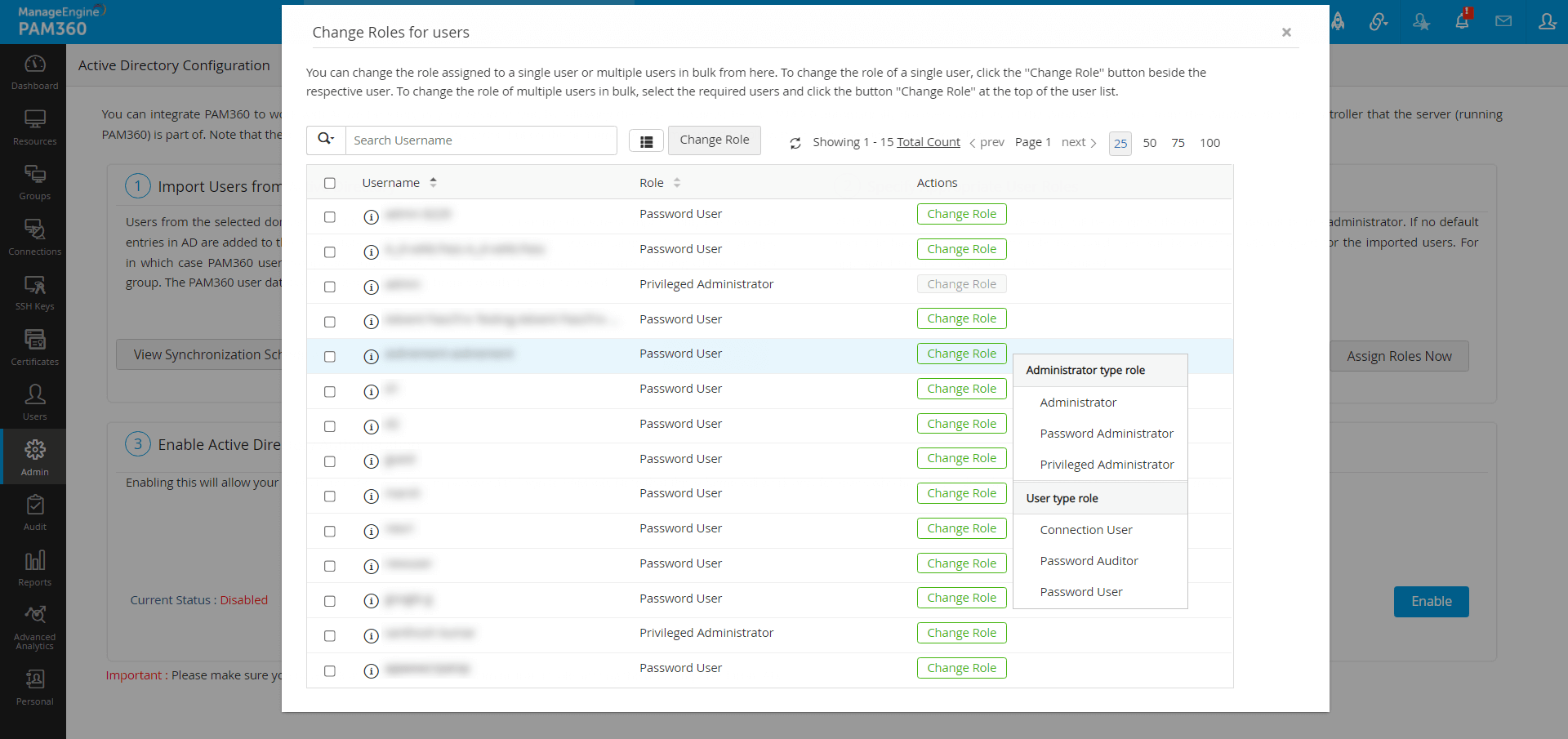
All the users imported from AD will be assigned the Password User role by default. To assign specific roles to specific users,
- Click the button Assign Roles Now.
- In the pop-up form that opens, all the users imported from AD are listed.
- Click Change role button against desired users for whom you wish to change the role and select the appropriate role from the drop down.
- Click Save and the required roles are set for the users.

3. Enabling AD Authentication
The third step is to enable AD authentication. This will allow your users to use their AD domain password to login to PAM360. Note that this scheme will work only for users who have been already imported to the local database from Active Directory.
Troubleshooting Tip
The browser will keep asking for Domain User credentials on the login page, if computer account credentials are incorrect. In that case, cancel the pop-up to access the PAM360 login page.