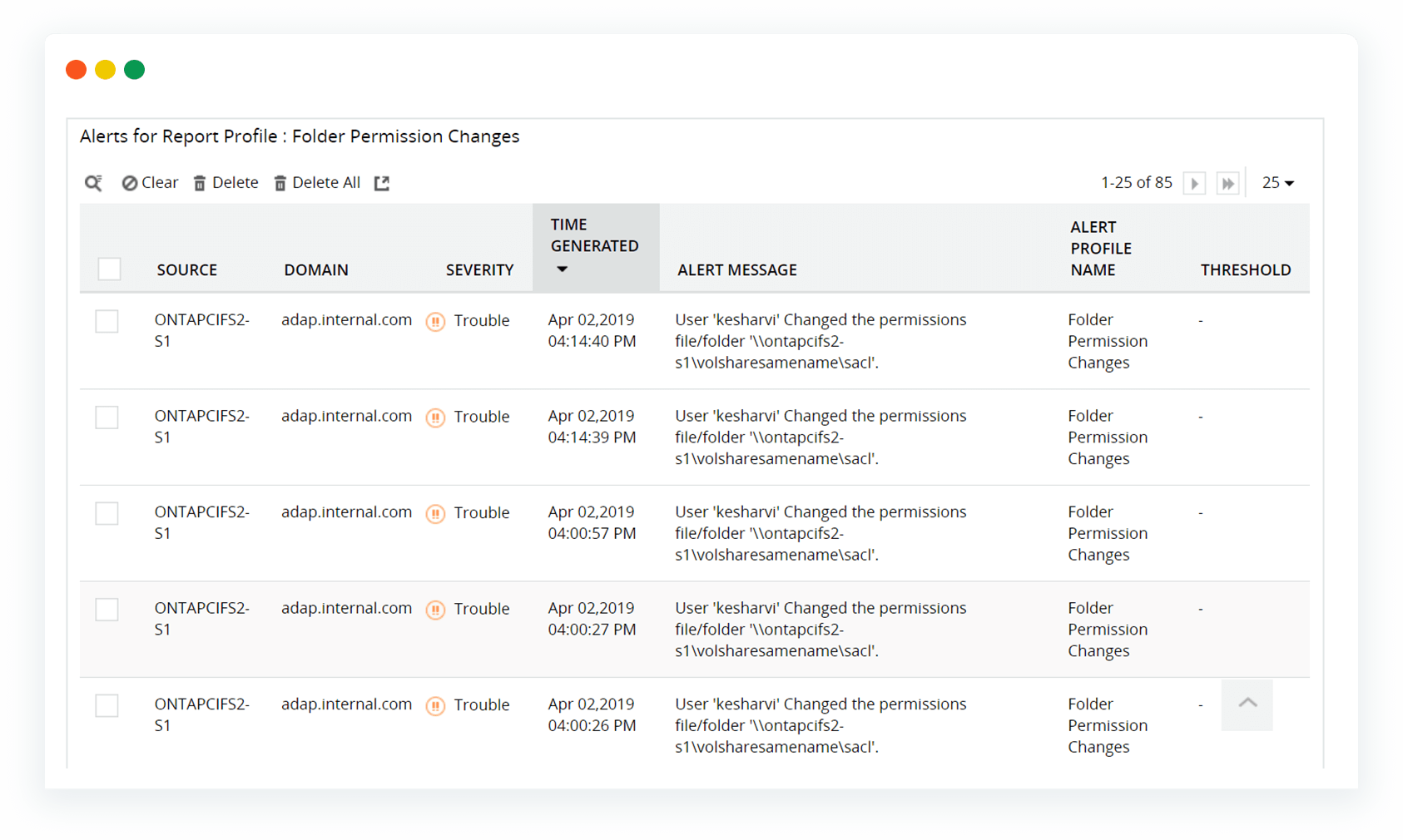
What you can do to prevent a breach.
Keep an eye on all NTFS permission changes to make sure that unwarranted access is not granted to anyone.
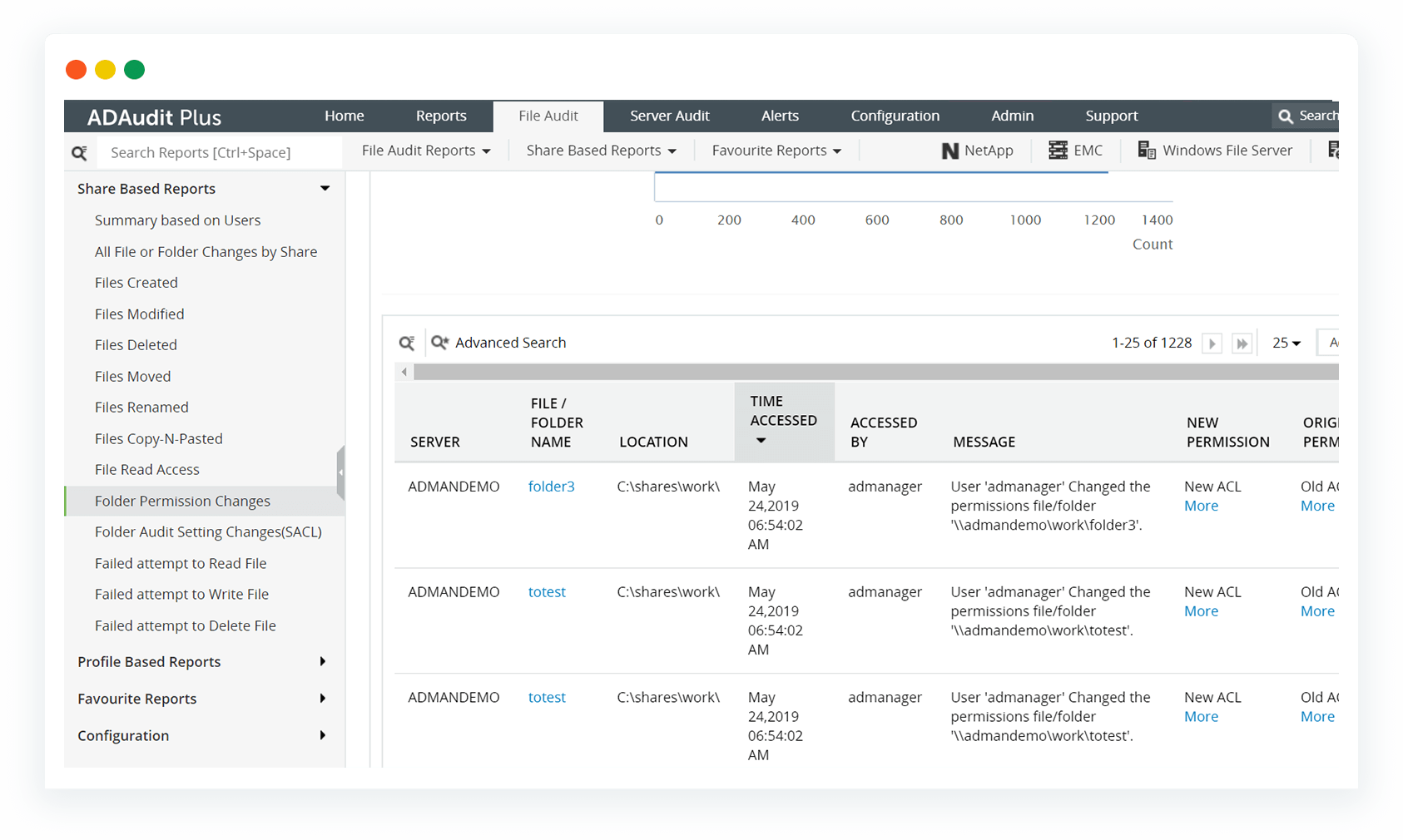
Be aware of who has what permissions, what objects the permissions apply to, and the level of control users have on sensitive files and shared folders.
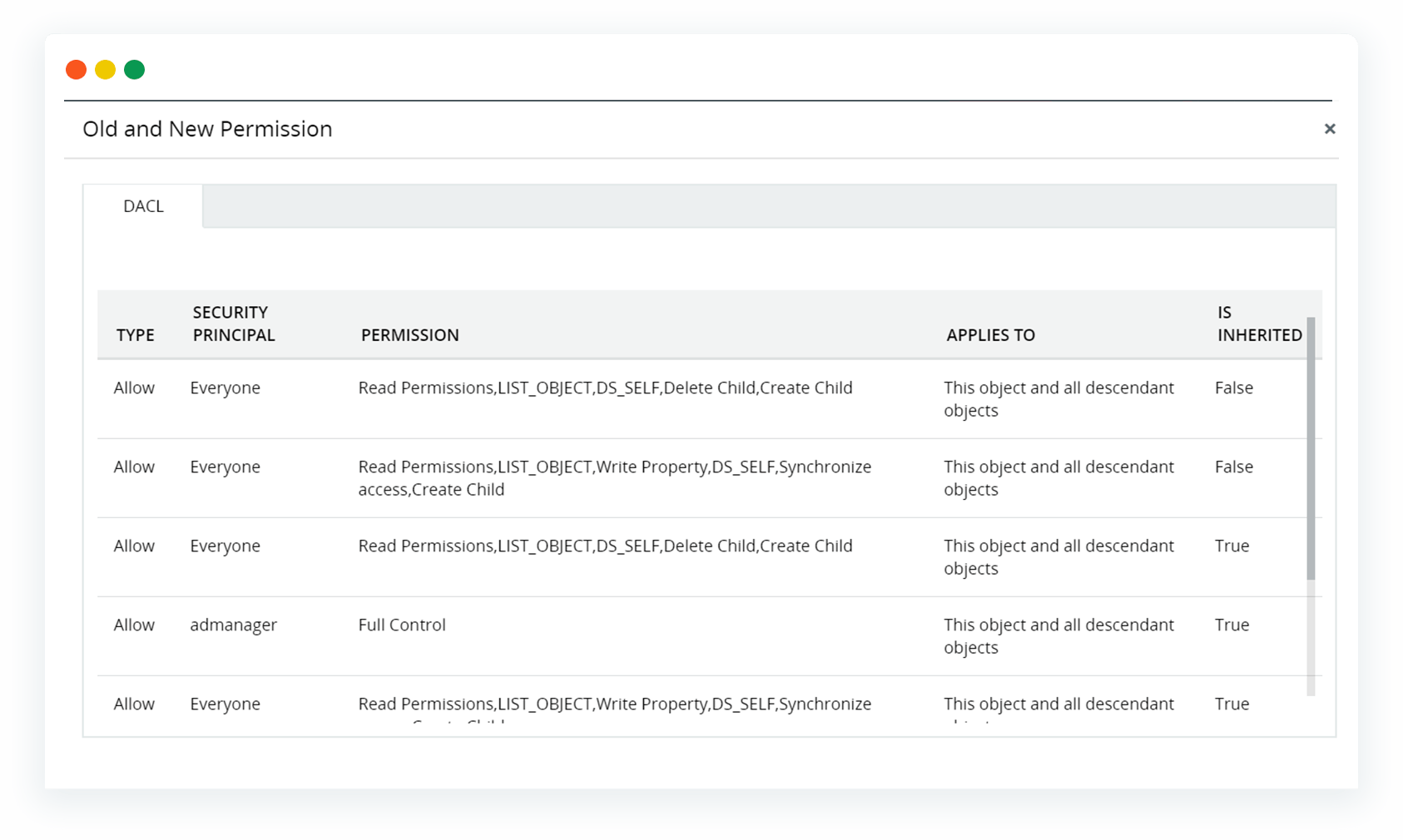
Be notified immediately if sensitive files are shared or NTFS permissions are modified to grant users more access than they need.